DDoS Mitigation
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic from multiple sources. DDoS attacks can exploit various layers of a network, including:
- Layer 3/4 (Network and Transport Layers): Protocol and packet exploitation to saturate network resources.
- Layer 7 (Application Layer): Targeted attacks that mimic legitimate traffic, such as CC attacks, brute force, and slow HTTP requests.
The following sections illustrate the effect of DDoS attacks under three protection scenarios: no protection, origin-level protection, and MaxiSafe protection.
Attacks without Protection
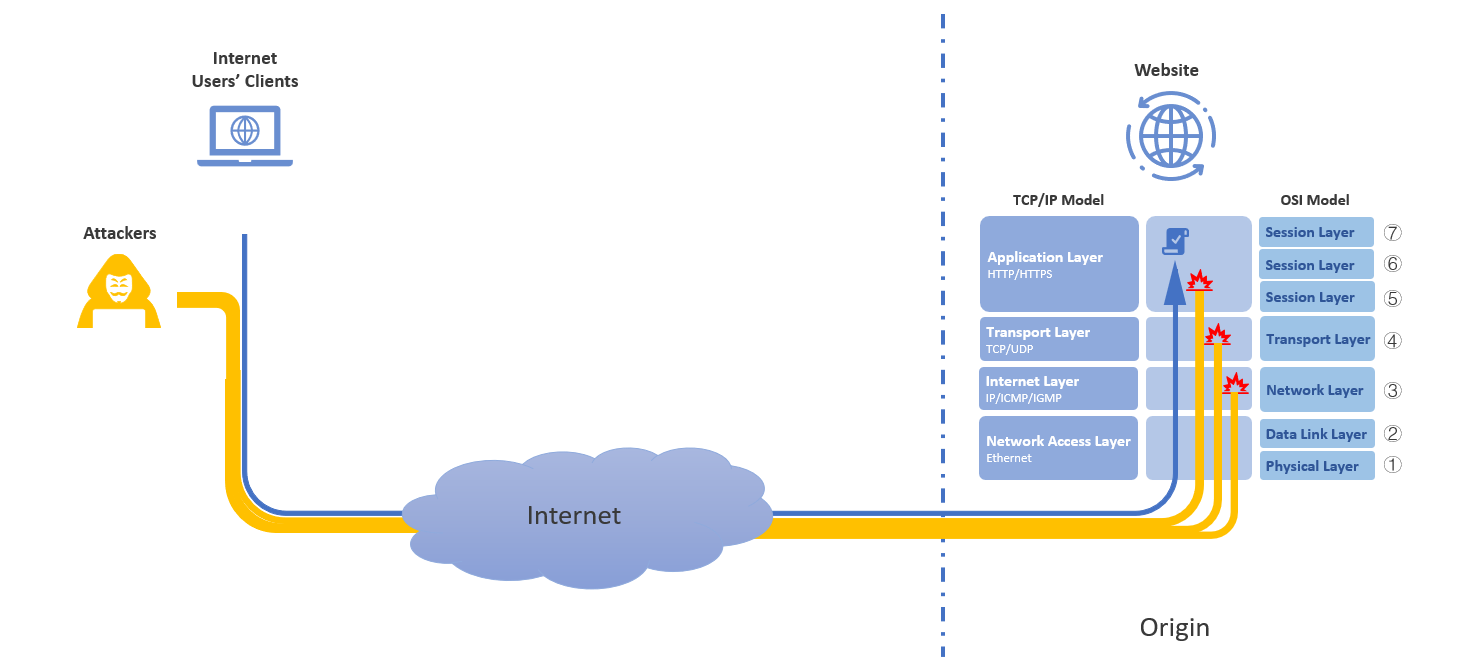
When no protection is in place, all traffic - whether legitimate or malicious - reaches the origin server directly. This exposes the website to attacks at multiple layers:
- Layer 3/4 (Network and Transport Layers): Floods and malformed packets exhaust bandwidth and connection resources, impacting network stability.
- Layer 7 (Application Layer): High-frequency or low-rate HTTP requests overwhelm application logic and exhaust server processing capacity.
The origin infrastructure becomes the sole point of load handling and attack absorption, increasing the likelihood of downtime, performance degradation, and service disruption.
Attacks Under Origin Protection
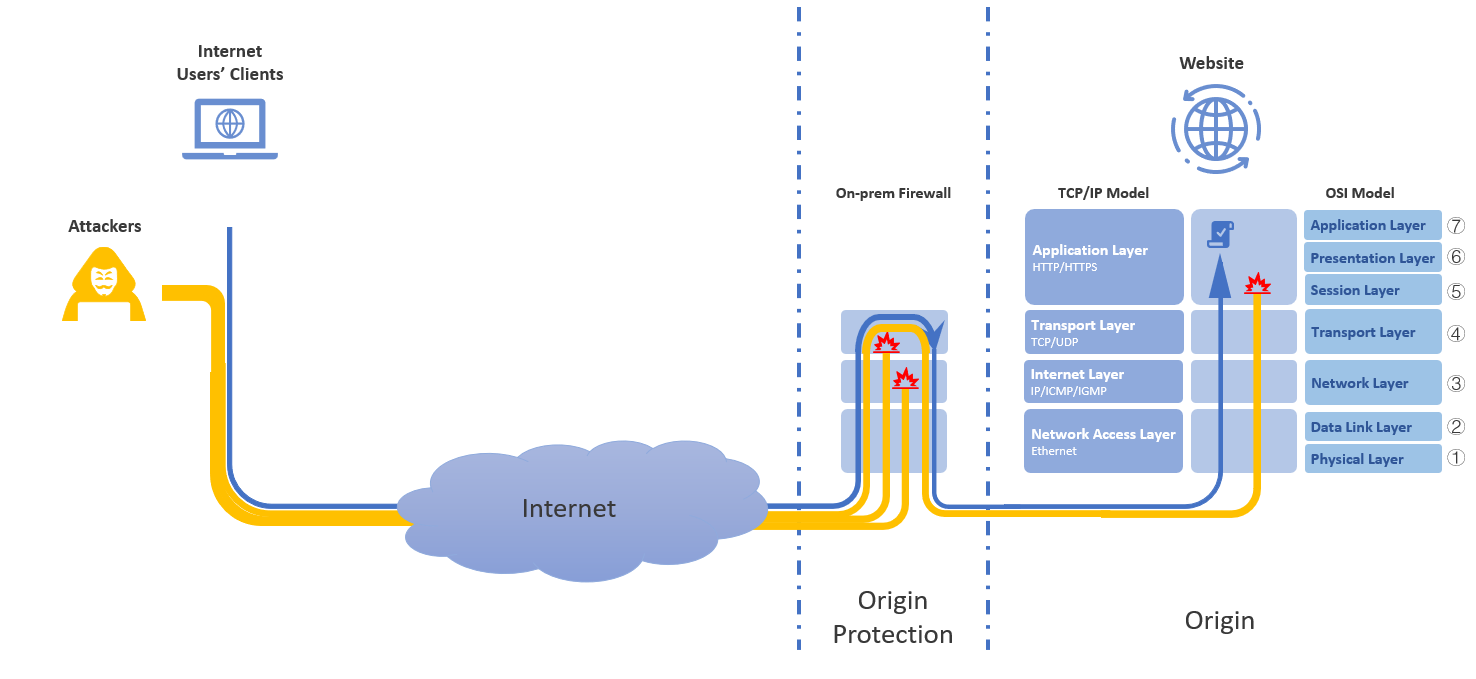
Website owners commonly deploy on-prem firewalls to defend against basic network-layer threats. These systems provide effective control at Layers 3/4 but lack the capabilities to mitigate advanced application-layer attacks.
Origin Protection with On-Prem Firewall
- Provides localised defence against Layer 3/4 attacks such as TCP/UDP floods and malformed IP packets.
- Enforces basic connection thresholds and rate limits to reduce volumetric overload on backend resources.
- Acts as a secondary filter for traffic that bypasses upstream defences.
- Cannot inspect or correlate Layer 5-7 traffic patterns, leaving applications exposed to session abuse, slow-rate exploits, and complex HTTP-based attacks.
Attacks Under MaxiSafe Protection
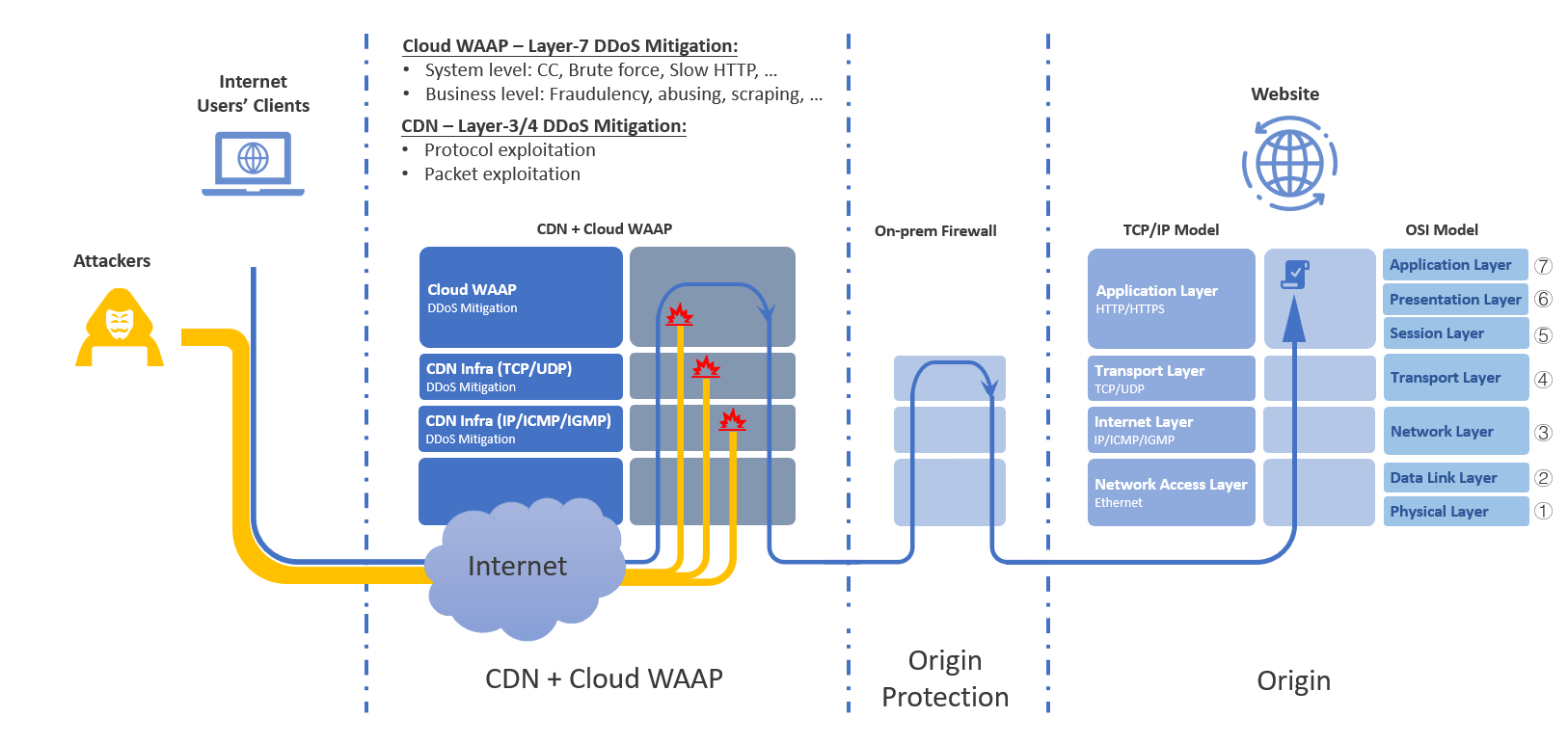
With MaxiSafe deployed, the integrated CDN and Cloud WAAP layer handles both network and application-layer threats before they reach the origin. This significantly reduces the attack surface by intercepting malicious traffic at the edge:
- Blocks threats from external and origin attackers before they reach the on-prem firewall or backend servers.
- Combines CDN infrastructure for Layer 3/4 protection with Cloud WAAP for advanced Layer 7 inspection and filtering.
CDN Infrastructure Protection
- Filters low-level protocol attacks to preserve network stability.
- Mitigates:
- TCP/UDP Floods: Intercepts high-volume traffic aimed at exhausting connection tables or ports.
- IP/ICMP/IGMP Abuse: Drops malformed or excessive packets used for scanning, spoofing, or amplification.
Cloud WAAP Protection
- Inspects HTTP/HTTPS traffic to detect abnormal behaviour and block application-layer threats.
- Mitigates:
- CC Attacks: Detects repetitive access patterns that simulate legitimate sessions to overload applications.
- Brute Force Attacks: Identifies high-frequency login attempts targeting authentication endpoints.
- Slow HTTP Attacks: Terminates connections designed to exhaust server threads by staying open.
- Business Logic Abuse: Blocks scraping, automation, and fraud attempts through request correlation and contextual analysis.
DDoS Mitigation Flow
- External DDoS traffic is first intercepted by CDN and Cloud WAAP, absorbing volumetric floods and filtering malicious requests.
- Layer 3/4 floods are absorbed by CDN infrastructure, preventing network saturation and maintaining service availability.
- Layer 7 application threats, including CC and brute force attacks, are mitigated at the Cloud WAAP level using advanced inspection and behavioural analysis.
- Residual Layer 4 attacks targeting the origin are further filtered by the On-Prem Firewall, ensuring comprehensive protection against direct-to-origin threats.